Pass4itsure has many years of exam experience! A group of professional ISC exam experts! Update ISC CISSP test questions throughout the year! The most complete ISC CISSP dumps https://www.pass4itsure.com/cissp.html test questions and answers! The safest buying experience! The biggest free sharing ISC CISSP exam practice questions and answers! Our goal is to help more people pass the exam!
ISC CISSP pdf free download https://drive.google.com/file/d/11V3AzKtiZ28MfwSGO-POM40HLj2__2EI/view?usp=sharing
Latest ISC CISSP exam dumps pdf [Google Drive]
[Latest PDF] ISC CISSP dumps pdf https://drive.google.com/file/d/11V3AzKtiZ28MfwSGO-POM40HLj2__2EI/view?usp=sharing
ISC CISSP practice test questions 1-13 free
QUESTION 1
During the risk assessment phase of the project, the CISO discovered that a college within the University is collecting
Protected Health Information (PHI) data via an application that was developed in-house. The college collecting this data
is
fully aware of the regulations for Health Insurance Portability and Accountability Act (HIPAA) and is fully compliant.
What is the best approach for the CISO?
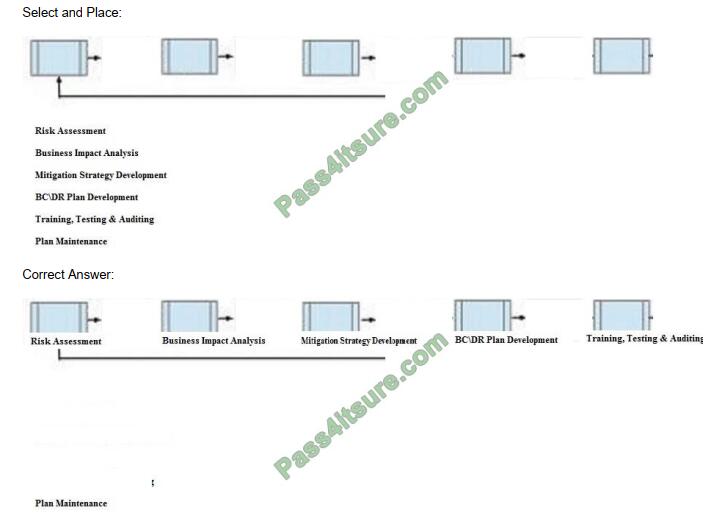
Below are the common phases to creating a Business Continuity/Disaster Recovery (BC/DR) plan. Drag the remaining
BC\DR phases to the appropriate corresponding location.
QUESTION 2
Which layer of the Open Systems Interconnection (OSI) model is being targeted in the event of a Synchronization (SYN)
flood attack?
A. Session
B. Transport
C. Network
D. Presentation
Correct Answer: B
QUESTION 3
When assessing an organization\\’s security policy according to standards established by the International Organization
for Standardization (ISO) 27001 and 27002, when can management responsibilities be defined?
A. Only when assets are clearly defined
B. Only when standards are defined
C. Only when controls are put in place
D. Only procedures are defined
Correct Answer: A
QUESTION 4
Which of the following is the PRIMARY issue when collecting detailed log information?
A. Logs may be unavailable when required
B. Timely review of the data is potentially difficult
C. Most systems and applications do not support logging
D. Logs do not provide sufficient details of the system and individual activities
Correct Answer: B
QUESTION 5
An application developer is deciding on the amount of idle session time that the application allows before a timeout. The
The BEST reason for determining the session timeout requirement is
A. organization policy.
B. industry best practices.
C. industry laws and regulations.
D. management feedback.
Correct Answer: A
QUESTION 6
While investigating a malicious event, only six days of audit logs from the last month were available. What policy should
be updated to address this problem?
A. Retention
B. Reporting
C. Recovery
D. Remediation
Correct Answer: A
QUESTION 7
A security architect plans to reference a Mandatory Access Control (MAC) model for implementation. This indicates that
which of the following properties is being prioritized?
A. Confidentiality
B. Integrity
C. Availability
D. Accessibility
Correct Answer: C
QUESTION 8
What should happen when an emergency change to a system must be performed?
A. The change must be given priority at the next meeting of the change control board.
B. Testing and approvals must be performed quickly.
C. The change must be performed immediately and then submitted to the change board.
D. The change is performed and a notation is made in the system log.
Correct Answer: B
QUESTION 9
When conducting a security assessment of access controls, Which activity is part of the data analysis phase?
A. Collect logs and reports.
B. Present solutions to address audit exceptions.
C. Categorize and Identify evidence gathered during the audit
D. Conduct statiscal sampling of data transactions.
Correct Answer: C
QUESTION 10
Which of the following alarm systems is recommended to detect intrusions through windows in a high-noise, occupied
environment?
A. Acoustic sensor
B. Motion sensor
C. Shock sensor
D. Photoelectric sensor
Correct Answer: C
QUESTION 11
Which of the following assures that rules are followed in an identity management architecture?
A. Policy database
B. Digital signature
C. Policy decision point
D. Policy enforcement point
Correct Answer: D
QUESTION 12
Which of the following is the BEST identity-as-a-service (IDaaS) solution for validating users?
A. Lightweight Directory Access Protocol (LDAP)
B. Security Assertion Markup Language (SAM.)
C. Single Sign-on (SSO)
D. Open Authentication (OAuth)
Correct Answer: A
QUESTION 13
Which of the following is the MOST effective attack against cryptographic hardware modules?
A. Plaintext
B. Brute force
C. Power analysis
D. Man-in-the-middle (MITM)
Correct Answer: C
Conclusion:
Free real ISC CISSP exam preparation materials, ISC CISSP practice exam + ISC CISSP pdf dumps. Use them correctly and you will not fail. Get the full ISC CISSP dumps https://www.pass4itsure.com/cissp.html ( Q&As: 970).
Free ISC CISSP dumps pdf download online!
https://drive.google.com/file/d/11V3AzKtiZ28MfwSGO-POM40HLj2__2EI/view?usp=sharing